Seed phrase and private key are two terms that are tightly related but are different things. When setting up a new crypto wallet such as Metamask, Ledger or Trezor, among others, a list of 12 or 24 common words is given to the user to back up. That list is the so-called seed phrase, an “easy to remember, easy to backup” word list.
A private key is a large binary string used by a crypto wallet for signing the transactions that later will be sent to the chain.
In this article we are going to take a journey from the generation of the seed phrase to the multiple wallet address generation, making a special stop at the private key creation and paying attention to the technical details of this process.
How is the seed phrase generated? The BIP39 proposal
BIP stands for Bitcoin Improvement Proposal. They are documents that describe a proposal for improving the Bitcoin blockchain ecosystem. BIP39 is called “Mnemonic code for generating deterministic keys” and describes the process of generating the mnemonic code. Here’s how it is done:

The words are taken from a word list that is available in several languages. The length of the list is always 2048 (2048 = 2¹¹, the number of bits used for grouping ENT + CS).
The quantity of words produced depends on the amount of entropy bits (ENT – the randomness factor of the initial seed). Typically the lengths used are 128 bits, leading to 12 words, and 256 bits, resulting in 24 words.
How is the private key generated?
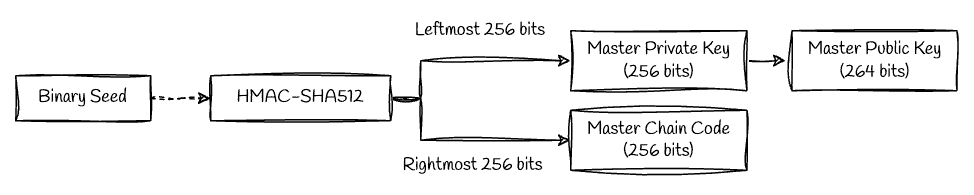
Binary seed
Once the mnemonic seed phrase is obtained, numerous private keys can be generated from it. That is why wallets such as Metamask and Trezor are able to generate any number of accounts needed with only one seed phrase.
To generate the private keys from the seed phrase, the initial step involves computing a binary seed derived from the mnemonic. This computation uses the key stretching algorithm PBKDF2 with HMAC-SHA512, where the seed phrase is concatenated with the string “mnemonic” and a password utilized as a salt. In instances where no password is utilized, only the term “mnemonic” is appended.

Employing PBKDF2 increases the time and computational power needed for brute-force attacks, rendering it highly impractical to utilize this approach for cracking a seed phrase.
It is worth mentioning that this process and the seed phrase generation are completely separated processes. This process can be used with a mnemonic seed generated from a totally different process.
Private keys
Now it is time to use the binary seed to generate private keys (and from those, public keys and wallet addresses). The following process describes what it is known as a HD Wallet (Hierarchical Deterministic Wallet). First we need to create a Master Private Key, a Master Public Key and a Master Chain Code from the Binary seed:
From this derivation we will produce all the accounts we need in a deterministic way. To create new accounts, we require:
- Either the Master Private Key or the Master Public Key.
- The Master Chain Code: this will be used as a source of entropy.
- A 32 bit integer number used as index.

In the diagram above we used the Master Private Key, but as said earlier we can also use the Master Public Key. The difference between using one or the order is generating a Hardened Key or a Normal Key, but that is out of the scope of this article.
We can create a virtually limitless quantity of private keys with this method either by changing the index or using a Child Key as a Master Key and repeat the process. This way we can have a tree of private keys.
Gluing it all together
We saw how a seed phrase is generated, used to generate a binary seed that then is used to generate a Master Private Key. This Master Private Key allows us to generate multiple Child Private Keys.
Public Keys and Wallet addresses are derived from Child Private Keys. It is a chain of derivation:

Does this mean that I always need a seed phrase to generate private keys? No! In fact, at the beginning of the blockchain era, all private keys were created individually.
Security
Is it worth trying to guess a seed phrase? Imagine that your seed phrase is composed of only one word of the word list. This means that the attacker has to try only 2048 combinations to derive your private key and steal all your assets. Suppose that deriving a private key with a specific combination takes 1 millisecond, then, it would take around 2 seconds to test all the possibilities!
Imagine now that your seed phrase is composed of two words of the word list. This means that the attacker has to try 2048 x 2048 = 2048² = 4194304 combinations to derive your private key. Assuming the 1-millisecond scenario, it would take the attacker around 1 hour and 10 minutes to test all the possibilities. That is a lot more!
Let’s repeat the process but now with 12 words. This means the attacker has to try 2048¹² = 5444517870735015415413993718908291383296 combinations. It would take around 2048¹²÷1000÷60÷60÷24÷365 ≈ 172644529132896227023528466479 years.
Conclusion
We saw the main difference between seed phrase vs private key, how it helps to keep your assets safe (by saving a phrase instead of a very long easy to forget number).
Are we at the end of the road? It doesn’t seem to be the case, even though this is a huge improvement on how wallets are created, managed and recovered it is still not enough to enable massive adoption of the crypto ecosystem. There are currently a lot of efforts to make the crypto space more user friendly. A proof of that is Ethereum’s ERC-4337, known as “account abstraction” that will, among other things, allow the user to use standard methods of authentication such as fingerprint instead of having to store a mnemonic phrase.
The crypto space traveled a long distance to be where it is today, but there’s still a lot ahead that needs to be explored, new methods to develop and new things to be discovered. In my opinion, this is just the beginning of this amazing trip. Even though mnemonic phrases are the way-to-go today, it is worth paying attention to the new solutions that arise from the community. One or many of those new ideas will help to on-board the next generation of users and allow the mass adoption of this amazing technology.
We are always looking for Web3 talent !
Mighty Block is one of the partners of Forte, a platform to enable game publishers to easily integrate blockchain technologies into their games. We believe blockchain will enable new economic and creative opportunities for gamers around the world and have assembled a team of proven veterans from across the industry (Kabam, Unity, GarageGames, ngmoco, Twitch, Disney), as well as a $100M developer fund & $725M funding, to help make it happen. That’s where you come into play.
Feel free to browse all our current open job opportunities in the following link 👇




